PT Network Attack Discovery

Provides network visibility

Detects hidden threats
The system automatically detects attacker attempts to penetrate the network and identifies hacker presence on infrastructure based on a wide range of indicators, including use of hacker tools and transmission of data to attacker servers.

Makes SOCs more effective

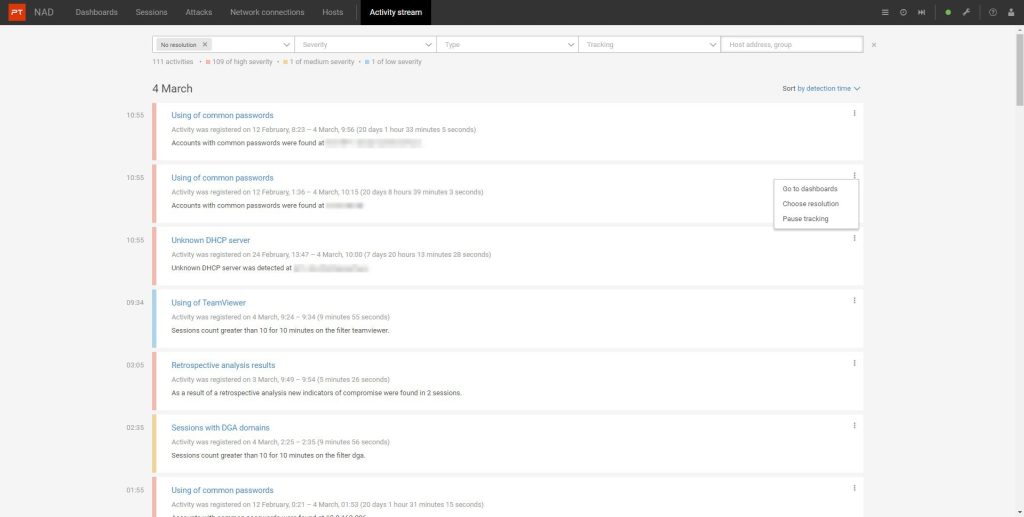
PT NAD users can see threat data in a single feed
With the new version of PT NAD, you can detect attacks using new analytics modules, collect up-to-date information about network hosts, and centrally learn about detected threats in a single feed.
Detects malicious activities in east/west traffic
PT NAD analyzes both north/south and east/west traffic and detects lateral movement, attempts to exploit vulnerabilities, and attacks against end users on the domain and internal services.
PT NAD detects

Threats in encrypted traffic
Thanks to advanced analytics, PT NAD pinpoints malware hidden by TLS or custom protocols.
Lateral movement
PT NAD detects attacker attempts to expand their presence by observing as they engage in reconnaissance, remote command execution, and Active Directory and Kerberos attacks.

Use of hacker tools
Exploitation of vulnerabilities

Malware activity

Past attacks
Malicious evasion from security tools
PT NAD detects DNS, HTTP, SMTP, and ICMP tunnels used by attackers to steal data, communicate with C&C servers, and hide their activity from security tools.

Connection to automatically generated domains

Non-compliance with IS policies
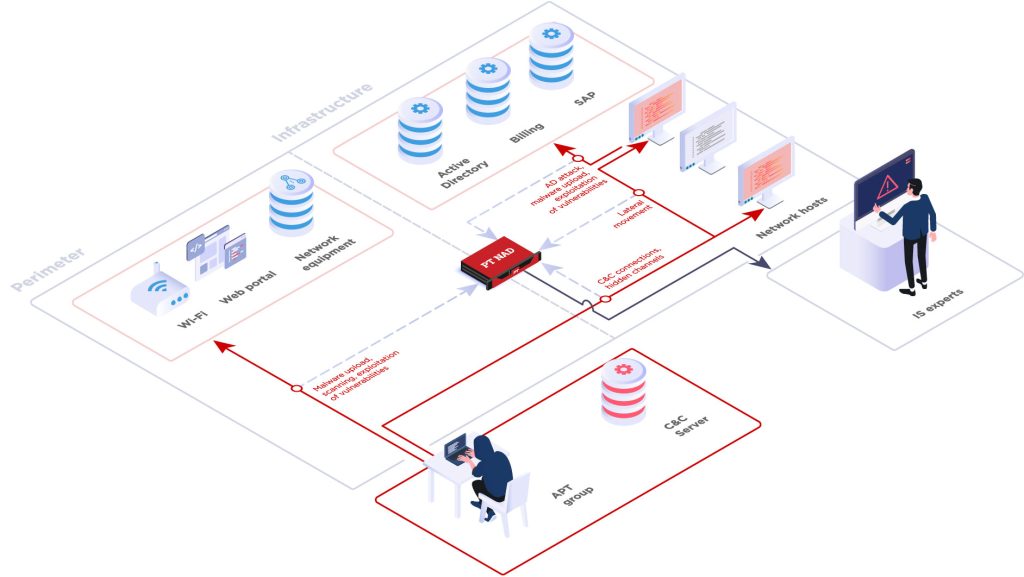
How PT NAD maps to MITRE ATT&CK
Learn how the network detection and response system PT Network Attack Detection can identify 117 adversary techniques described in MITRE ATT&CK.
Detects even modified malware
PT NAD alerts about all dangerous threats and detects even modified versions of malware. To describe the full range of cyberthreats, our experts constantly explore the latest malware samples and hacker tools, techniques, and procedures. Each rule they create covers an entire malware family.
How it works
Keeps attacks private
PT NAD detects IT configuration flaws and cases of non-compliance with security policies, which otherwise can offer attackers a way in. Filters help to quickly identify credentials stored in cleartext, weak passwords, remote access utilities, and tools that hide network activity. Pin filters of interest in a separate widget for quick reference. Here is a widget displaying all non-encrypted passwords:

Thanks to embedded machine learning technologies, advanced analytics, unique threat detection rules, indicators of compromise, and retrospective analysis, PT NAD detects attacks both at the earliest stages and after attackers have already burrowed into infrastructure.
The PT Expert Security Center updates rules and indicators of compromise twice a week. Updating the database does not require a constant connection to the Positive Technologies cloud.
Advanced analytics modules enable identification of complex threats and network anomalies. They take into account many parameters of the attacker’s behavior and are not tied to the analysis of individual sessions, unlike the rules for attack detection.

Because PT NAD saves copies of raw traffic and session data, forensic investigators can:
- Localize attacks.
- Reconstruct kill chains.
- Detect vulnerabilities in infrastructure.
- Take measures to prevent similar attacks.
- Gather evidence of malicious activity.

PT NAD is ideal for threat hunting and detecting hidden threats that standard cybersecurity tools miss. A security analyst, possessing the necessary skills and infrastructure-specific knowledge, can empirically test hypotheses. So PT NAD makes it possible to determine whether a hacker group, insider threat, or data breach is truly present, and if the hypothesis is confirmed, take proactive measures accordingly.

Key features
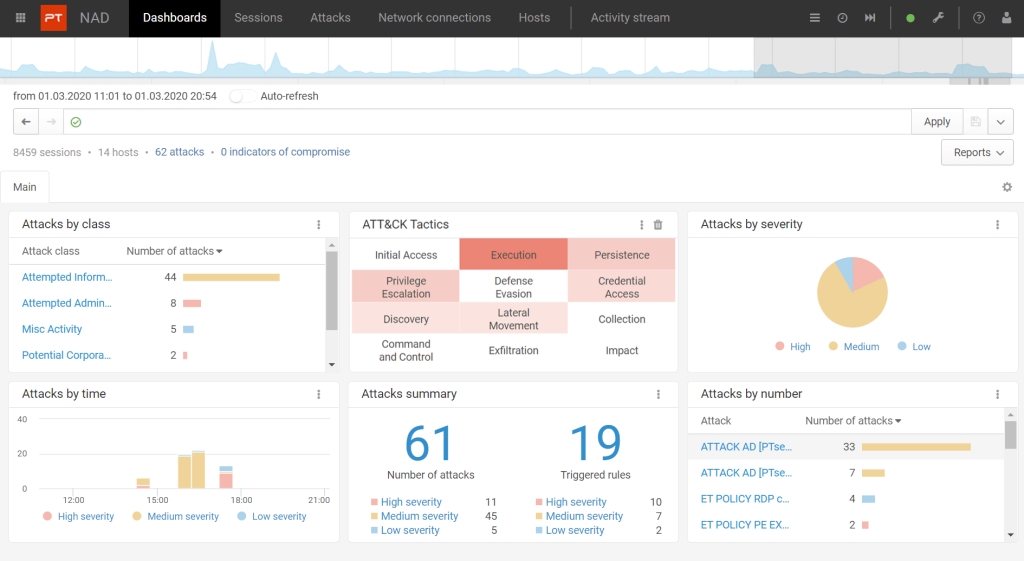
Attack detection
The system informs of incidents and automatically assesses how dangerous they are. The dashboard provides key information about all attacks: how many, which types, the degree of danger, and when they occurred. Click to view details for any attack.
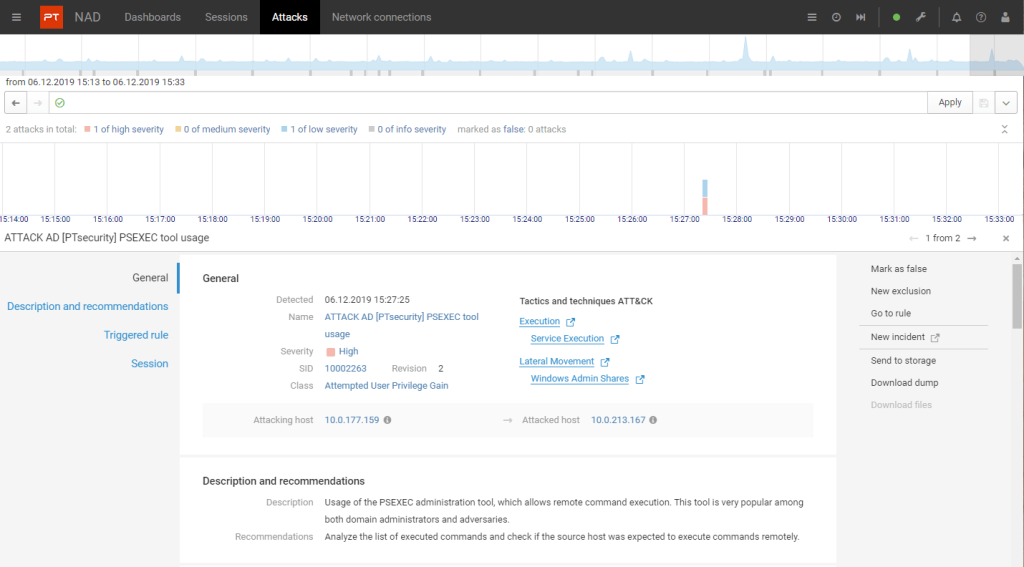
Response at a glance
Information for each attack shows the affected hosts, event time, session data, and hacker tools, techniques, and procedures (TTPs) per the MITRE ATT&CK classification. With attack staging information, you can take the right surgical measures to get the job done.
Learn about new attacks and threats in a single feed

Monitor network hosts
Session filtering
Filtering sessions offers a way to look for malicious activity, indicators of compromise, and configuration errors. PT NAD can quickly sort through sessions by any of 1,200 parameters and display detailed information for each.