

Allows to flexibly customize virtual environments to match real workstations. This ensures high fidelity and detection even if malware is tailored to a specific company’s infrastructure.
Once databases are updated, PT Sandbox automatically re-checks previously analyzed files and detects hidden threats and previously unnoticed attacks.
PT Sandbox checks all traffic generated during analysis of a suspicious file and decrypts TLS traffic to detect malicious activity.
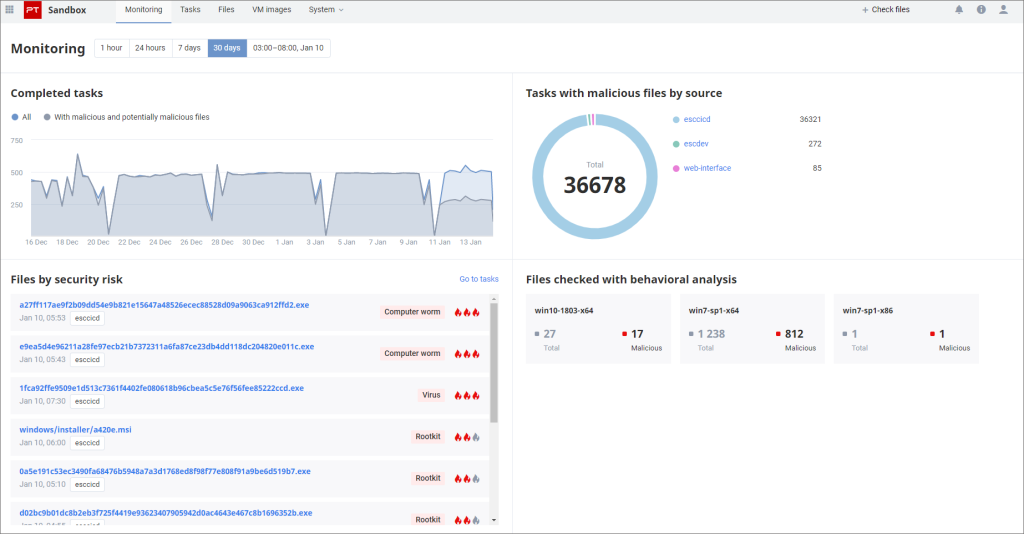
PT Sandbox blocks all the main vectors used by malware to infiltrate your network. The product analyzes email attachments, network stored files, files uploaded to corporate sites, and Internet downloads.

Submit your email for the latest collection and latest articles in the field of security.
Secure Way has been with more than twenty years of experience in the field of information technology security and with the aim of providing advanced and intelligent security services and products in a new company.
All rights reserved and owned by Secure Way, Any copying is prosecuted.