MaxPatrol VM
MaxPatrol VM is a next-generation vulnerability management system. The solution allows you to build a full-fledged vulnerability management process and control it during both routine operation and urgent scanning.
VMNG—what's changed?
How to detect and manage vulnerabilities is of concern to any infosec professional, regardless of industry. To address these tasks, companies use security analysis tools. They perform a deep scan of all systems in automated mode to identify vulnerabilities and hardware configuration errors. Nevertheless, issues remain after scanning. To implement vulnerability management, it is also necessary to decide which vulnerabilities are most critical for the infrastructure, what to start with, how to correctly prioritize elimination tasks, and how to assess what actions affect the company’s security level. Next-generation vulnerability management systems are able not only to identify vulnerabilities in good time, but also help to build the entire vulnerability management process.
Product overview
MaxPatrol VM is a next-generation vulnerability management system. The solution allows you to build a full-fledged vulnerability management process and control it during both routine operation and urgent scanning.
With MaxPatrol VM you can:
- Get complete and continuously updated data on the IT infrastructure.
- Factor in the significance of protected assets.
- Identify, prioritize, and set vulnerability processing rules for the IT department.
- Control vulnerability elimination.
- Monitor the company’s overall security level.
MaxPatrol VM is based on the unique security asset management (SAM) technology. This allows MaxPatrol VM, using active and passive data collection, to build at any moment a complete and continuously updated model of the IT infrastructure under observation. By understanding the IT environment, the solution adopts and automates vulnerability management across all company systems, taking into account the importance of network components and infrastructure changes.
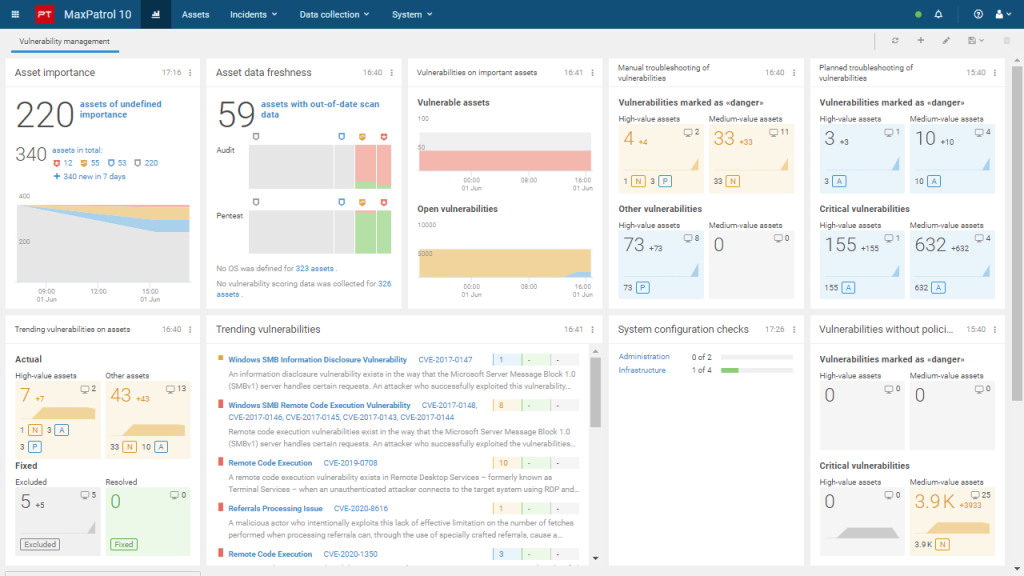
How it works

Collects and maintains an up-to-date asset database

Evaluates and classifies assets

Identifies and prioritizes vulnerabilities

Defines policies

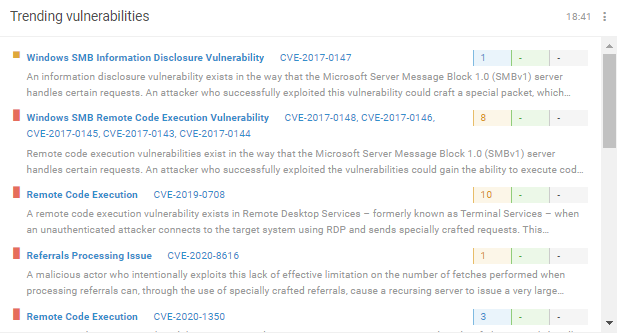
Monitors trending vulnerabilities
Controls vulnerability management
Application scenarios
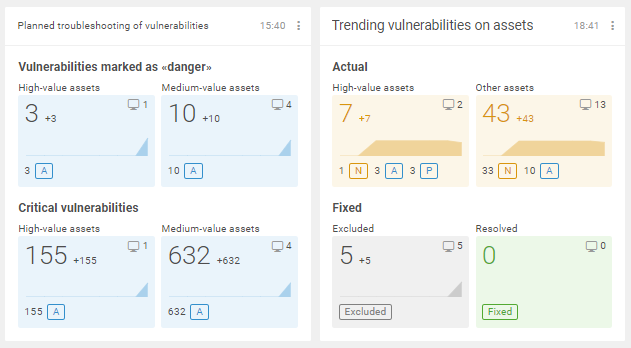
Learn about trending vulnerabilities
Positive Technologies selects and reports the most relevant critical vulnerabilities for urgent scanning. Infosec experts will not have to waste time studying external resources—they will already be aware of new dangerous vulnerabilities.

Monitor the security of critical assets
Control vulnerability elimination