Positive Technologies has released the next version of PT Network Attack Discovery (10.1), a system for deep traffic analysis. With it, you can detect attacks using new analytics modules, collect up-to-date information about network hosts, and centrally learn about detected threats in a single feed.
Activity feed
To enable users to learn about new attacks and threats in a timely manner, a new section—an activity feed—has been added to PT NAD. The feed collects a list of identified threats in one place, combines messages about similar activities into one, and allows you to manage them. You can mark the issue as resolved or no longer track such activity.
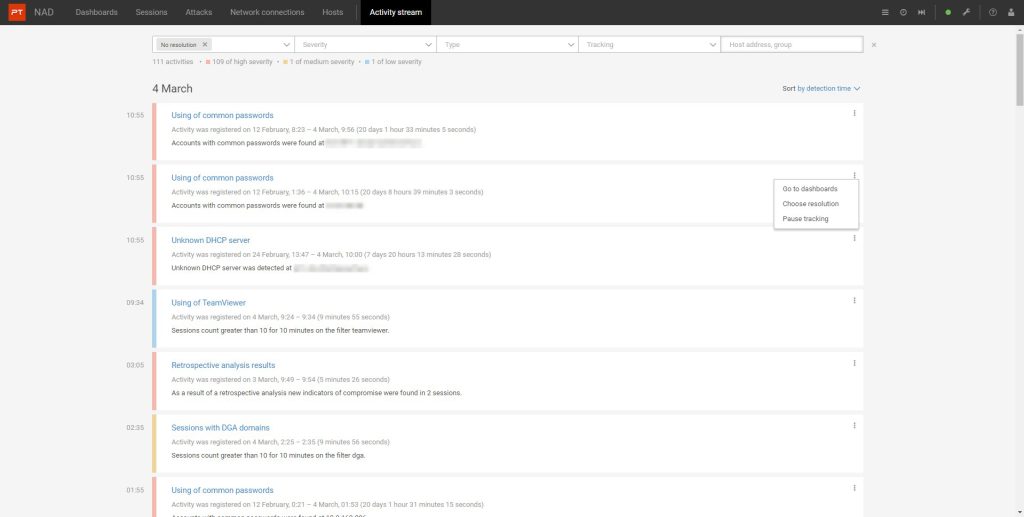
In PT NAD version 10.1, messages appear in the feed when:
- Users use dictionary passwords on the network.
- The indicators of compromise are triggered during the retrospective analysis.
- An unknown DHCP server 1 appears on the network: the server might be fake, and by using it attackers can intercept traffic and obtain user credentials.
- The traffic filtering conditions that the user has set in advance are triggered. In this way, you can receive notifications about any activity of interest on the network, such as connections to certain phishing domains, transmission of large amounts of information from database servers, and actions of specific users.
New mechanisms of attack detection
The new version of PT NAD adds deep traffic analytics modules that enable identification of complex threats. They take into account many parameters of the attacker’s behavior and are not tied to the analysis of individual sessions, unlike the rules for attack detection. With the help of the modules, the product automatically detects abnormal LDAP requests. 2 Such requests can be used by attackers during reconnaissance to collect information about the domain: about users, their groups, network hosts, and passwords.
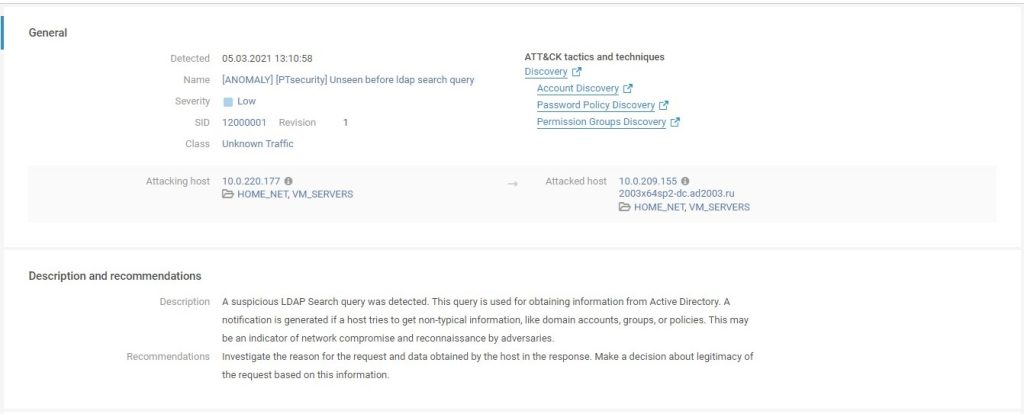
With the help of new detection mechanisms, the product also detects the use of dictionary passwords and unknown DHCP servers. Information about such events is included in the activity feed.
In the next version of PT NAD, analytics modules will be used to identify 30 more types of threats.
Monitoring network hosts

Network transparency is now even higher
For greater transparency of internal and external traffic, the new version of PT NAD has an expanded list of identified and parsed protocols. The product detects five more new protocols that are found on the networks of Russian companies. There are now 85 identified protocols in total.
PT NAD parses four more new protocols, collecting additional data about the connections that are established via such protocols. The analysis of the new protocols gives an understanding of what is happening on the network, for example, which Google services users connect to, what requests are sent during remote command execution, whether this is legitimate activity or compromise by attackers.
PT NAD 10.1 identifies encrypted traffic that is transmitted via nonstandard protocols. This is necessary to draw the attention of the system operator to suspicious unknown activity on the network. It is possible that the attackers encrypt the traffic using their own protocols, and thus try to cover their tracks.
Other improvements
- PT NAD 10.1 is localized into English.
- You can now set the time zone—the settings are applied to the user account.
- From the PT NAD interface, you can go to PT Sandbox in one click and view detailed information about the detected malicious file.

